plami666
Потребител-
Брой теми
14 -
Регистрация
-
Последно посещение
plami666's Achievements
Новобранец (1/14)
0
Репутация в общността
-
Премахване на троянски кон
plami666 replied to plami666's тема in Компютърна сигурност и защита от зловреден код
Да,сега го открих и исках да го изтрия,но ми изписва:Error Deleting File or Folder Cannot delete panda2_0dn.dll:Access is denied. Make sure the disk is not full or write-protected and that the file is not currently in use. -
Премахване на троянски кон
plami666 replied to plami666's тема in Компютърна сигурност и защита от зловреден код
Добре,а как мога да го премахна тъй като го търсих и с търсачката,но не открива файла.. -
Премахване на троянски кон
plami666 replied to plami666's тема in Компютърна сигурност и защита от зловреден код
Да,получаваше се при новата версия на Firefox,но сега всичко се оправи Но отново се появяват известията от avast!,че е блокиран троянски кон -
Премахване на троянски кон
plami666 replied to plami666's тема in Компютърна сигурност и защита от зловреден код
-
Премахване на троянски кон
plami666 replied to plami666's тема in Компютърна сигурност и защита от зловреден код
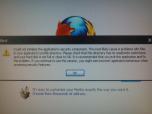
Когато пусна Firefox ми изписва това:Could not initialize the application's security component. The most likely cause is problems with files in your application's profile directory. Please check that this directory has no read/write restrictions and your hard disk is not full or close to full. It is recommended that you exit the application and fix the problem. If you continue to use this session, you might see incorrect application behaviour when accessing security features. Също не може да зарежда сайтовете. http://www.4shared.com/file/8r6ZO5kS/JavaRa.html? -
Премахване на троянски кон
plami666 replied to plami666's тема in Компютърна сигурност и защита от зловреден код
Сега не,но преди доста забиваше -
Премахване на троянски кон
plami666 replied to plami666's тема in Компютърна сигурност и защита от зловреден код
..checkup.txt -
Премахване на троянски кон
plami666 replied to plami666's тема in Компютърна сигурност и защита от зловреден код
Да компютърът често забиваcheckup.txt log.txt -
Премахване на троянски кон
plami666 replied to plami666's тема in Компютърна сигурност и защита от зловреден код
/AdwCleanerS1.txt JRT.txt -
Премахване на троянски кон
plami666 replied to plami666's тема in Компютърна сигурност и защита от зловреден код
http://www.4shared.com/file/OAlAs-02/hgfh.html? http://www.4shared.com/file/Ow_dBwp5/12012012_093622.html? -
Премахване на троянски кон
plami666 replied to plami666's тема in Компютърна сигурност и защита от зловреден код
За съжаление не мога да кача файловете,защото ми изписва Не Ви е позволено да качвате такъв тип файлове SHA256: 2ba9d2aba2b691510ad889ec62ad4d4a55bf2d60dd24112fcb2972987dff4323 File name: panda2_0dn.exe Detection ratio: 0 / 45 Analysis date: 2012-12-01 15:23:40 UTC ( 0 минути ago ) -
Премахване на троянски кон
plami666 replied to plami666's тема in Компютърна сигурност и защита от зловреден код
ssdeep 3072:AoW/uV1PAzLG1nHLK8U0dPsm+tyJXDO7huaxf6xM5lelVD5pq:A7/a+gnrK8HPsP8sk9xked8 TrID Win64 Executable Generic (59.6%) Win32 Executable MS Visual C++ (generic) (26.2%) Win32 Executable Generic (5.9%) Win32 Dynamic Link Library (generic) (5.2%) Generic Win/DOS Executable (1.3%) ExifTool SubsystemVersion.........: 5.0 InitializedDataSize......: 88064 ImageVersion.............: 0.0 ProductName..............: Panda Security URL Filtering FileVersionNumber........: 1.0.0.128 UninitializedDataSize....: 0 LanguageCode.............: English (U.S.) FileFlagsMask............: 0x003f CharacterSet.............: Unicode LinkerVersion............: 9.0 MIMEType.................: application/octet-stream Subsystem................: Windows GUI FileVersion..............: 1, 0, 0, 128 TimeStamp................: 2010:12:08 16:53:43+00:00 FileType.................: Win32 EXE PEType...................: PE32 ProductVersion...........: 1.0 FileDescription..........: Panda Security URL Filtering OSVersion................: 5.0 FileOS...................: Win32 LegalCopyright...........: Copyright © 2010 Visicom Media Inc. MachineType..............: Intel 386 or later, and compatibles CompanyName..............: Panda Security CodeSize.................: 129536 FileSubtype..............: 0 ProductVersionNumber.....: 1.0.0.0 EntryPoint...............: 0x12082 ObjectFileType...........: Executable application Sigcheck publisher................: Panda Security product..................: Panda Security URL Filtering description..............: Panda Security URL Filtering file version.............: 1, 0, 0, 128 signing date.............: 7:14 PM 12/8/2010 signers..................: Visicom Media Inc. copyright................: Copyright © 2010 Visicom Media Inc. Portable Executable structural information Compilation timedatestamp.....: 2010-12-08 16:53:43 Target machine................: 0x14C (Intel 386 or later processors and compatible processors) Entry point address...........: 0x00012082 PE Sections...................: Name Virtual Address Virtual Size Raw Size Entropy MD5 .text 4096 129186 129536 6.58 e0277b0f0ca67ac852e5dd3f0e050a0e .rdata 135168 29118 29184 4.97 01d7b739017b2dac110d7b651ff3bf20 .data 167936 12356 5120 2.20 28ad4798c50c8530a635c676024a6ead .rsrc 184320 42664 43008 4.87 643a2e4f9d59cf236870774bd0d9a266 .reloc 229376 10626 10752 5.22 557dff4bf41dcb3a70ad08269c3dc2ae PE Imports....................: [[VERSION.dll]] GetFileVersionInfoSizeA, GetFileVersionInfoA, VerQueryValueA [[WININET.dll]] HttpSendRequestA, HttpOpenRequestA, InternetReadFile, InternetCloseHandle, InternetOpenA, InternetConnectA, HttpQueryInfoA [[ADVAPI32.dll]] RegOpenKeyA, ConvertStringSecurityDescriptorToSecurityDescriptorW, RegSetValueExA, RegQueryValueExA, GetSecurityDescriptorSacl, RegDeleteValueA, RegCreateKeyExA, RegOpenKeyExA, RegCloseKey, SetSecurityInfo [[KERNEL32.dll]] GetStdHandle, GetConsoleOutputCP, GetFileAttributesA, FreeEnvironmentStringsA, DeleteCriticalSection, GetCurrentProcess, GetConsoleMode, GetLocaleInfoA, FreeEnvironmentStringsW, SetStdHandle, GetCPInfo, GetStringTypeA, WriteFile, GetSystemTimeAsFileTime, HeapReAlloc, GetStringTypeW, GetOEMCP, LocalFree, MoveFileA, InitializeCriticalSection, FindClose, TlsGetValue, SetLastError, CopyFileA, HeapAlloc, GetVersionExA, GetModuleFileNameA, UnhandledExceptionFilter, InterlockedDecrement, MultiByteToWideChar, CreateMutexA, SetUnhandledExceptionFilter, SetEnvironmentVariableA, TerminateProcess, WriteConsoleA, GlobalAlloc, LocalFileTimeToFileTime, SetEndOfFile, GetCurrentThreadId, LeaveCriticalSection, WriteConsoleW, InitializeCriticalSectionAndSpinCount, HeapFree, EnterCriticalSection, SetHandleCount, FreeLibrary, QueryPerformanceCounter, GetTickCount, TlsAlloc, FlushFileBuffers, LoadLibraryA, RtlUnwind, GetStartupInfoA, CreateDirectoryA, DeleteFileA, GetProcAddress, GetProcessHeap, CompareStringW, FindFirstFileA, CompareStringA, CreateFileMappingA, FindNextFileA, GetTimeZoneInformation, IsDebuggerPresent, GetFileType, TlsSetValue, CreateFileA, ExitProcess, InterlockedIncrement, GetLastError, SystemTimeToFileTime, LCMapStringW, HeapCreate, GlobalFree, GetConsoleCP, LCMapStringA, GetEnvironmentStringsW, RemoveDirectoryA, GetEnvironmentStrings, GetCurrentProcessId, SetFileTime, GetCurrentDirectoryA, HeapSize, GetCommandLineA, OpenMutexA, RaiseException, MapViewOfFile, TlsFree, SetFilePointer, ReadFile, CloseHandle, GetACP, GetModuleHandleW, WideCharToMultiByte, IsValidCodePage, UnmapViewOfFile, VirtualFree, Sleep, VirtualAlloc [[sHELL32.dll]] ShellExecuteA, SHGetFolderPathA [[uSER32.dll]] wsprintfA, SetTimer, GetLastInputInfo, LoadIconA, DispatchMessageA, IsDlgButtonChecked, MessageBoxA, SendMessageA, KillTimer, PeekMessageA, GetDlgItem, CreateDialogParamA, TranslateMessage, SetWindowTextA, ShowWindow, SetClassLongA, CheckDlgButton, IsDialogMessageA, DestroyWindow [[COMCTL32.dll]] Ord(17) PE Resources..................: Resource type Number of resources RT_CURSOR 16 RT_GROUP_CURSOR 15 RT_STRING 13 RT_ICON 8 RT_DIALOG 3 RT_BITMAP 2 RT_MANIFEST 1 RT_VERSION 1 RT_GROUP_ICON 1 Resource language Number of resources ENGLISH US 50 NEUTRAL 10 OTL.Txt Extras.Txt -
Премахване на троянски кон
plami666 replied to plami666's тема in Компютърна сигурност и защита от зловреден код
Ето..attach.txt dds.txt mbam-log-2012-11-30 (09-12-13).txt -
C:\Documents and Settings\All Users\Applicaton Data\Panda Security Toolbar Antiphishing\panda2_0dn.exе Това е вирусът,пробвах какви ли не начини да го премахна не става. Сканирах с tdsskiller и Malwarebytes Anti-Malware не могат да го открият, а avast! го намира, но не може да го премахне само изписва Блокиран троянски кон... Моля помогнете..